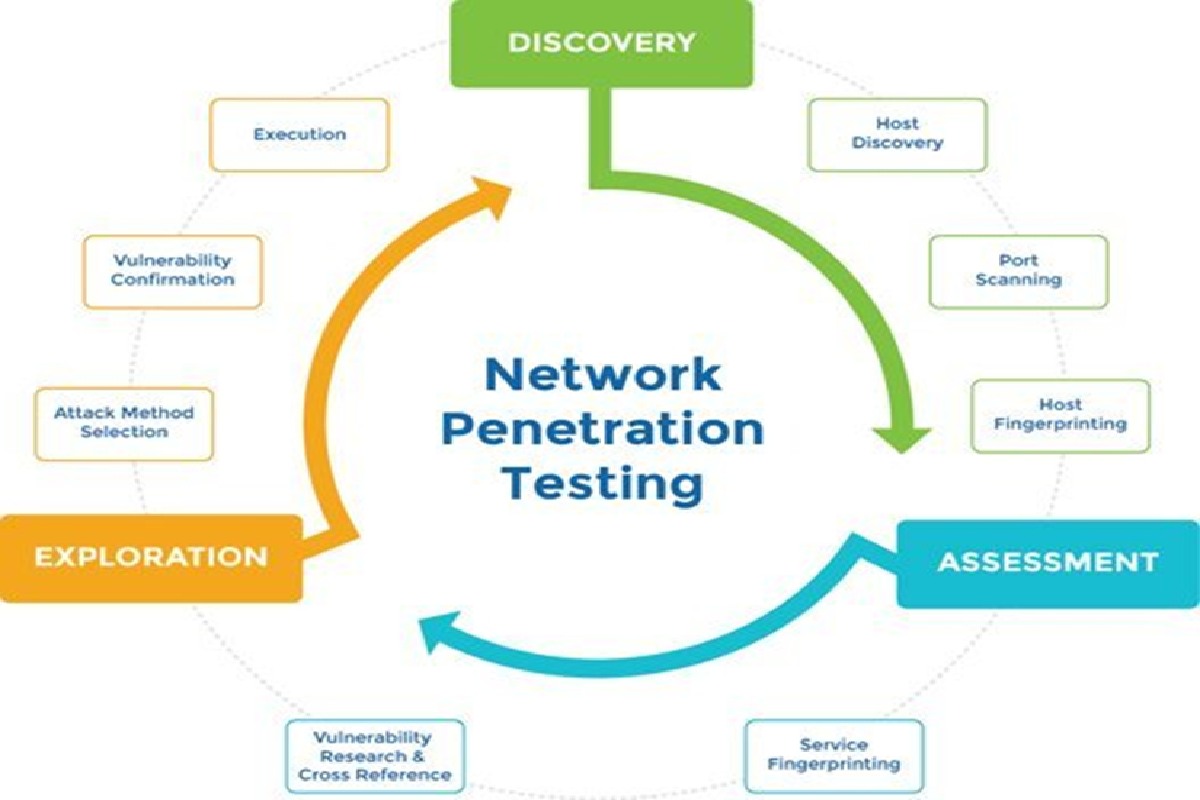
Network Penetration Testing – Before conducting network penetration testing, it’s important to evaluate the globally accepted industry-standard compliance rules and regulations that are suited for your firm. The basic network penetration testing methodology is usually the Penetration Testing Execution Standard (PTES) which combines the results from manual testing with the best testing tools available in the industry.
The purpose of a network penetration testing procedure is to identify and detect security vulnerabilities, design attack vectors, and find configuration errors and security issues in the business logic. At the end of the pentesting process, the risk of sensitive data breaches, unauthorized access via weak entry points, and the occurrence of cyberattacks must be reduced for maximum productivity from your network devices.
Table of Contents
How to perform network penetration testing?
The most effective and comprehensive network penetration testing methodology will be a combination of both automated and manual testing techniques through a series of five steps – reconnaissance, design of attack methods, vulnerability analysis, exploitation, and preparing the final report.
Reconnaissance (Gathering Information)
The basic sources of information before conducting a network penetration testing process are server fingerprinting, identifying the number of networks, search engine information, operating systems, and initial device footprinting. This will provide a finalized list of metadata and raw output which will help in mapping the environment and identifying a list of vulnerabilities to be exploited further.
Testing teams usually use discovery tools for passive information on the network and conduct active scans for listing the available services and vulnerabilities for designing the security assessment process.
Designing the attack methods
After gathering background information on the network, the ethical hacking team will finalize the list of vulnerabilities with a combination of manual and active testing methods. Assets are listed and prioritized into categories which include financial information, sensitive data, personal details of customers, business secrets, etc.
Here, testers utilize the network devices to map out all the available operating systems, open ports and services, and other potentially weak entry points. Open-source, commercial, or internally developed testing tools are used to pinpoint the security vulnerabilities with the help of information from the features and capabilities of different areas of the company network. This will help in establishing different threat categories depending on the severity of the security risk such as compromised user/employee credentials, lack of updates in outdated third-party components, session hijacking risks, etc.
Analyzing the discovered vulnerabilities
Here, each vulnerability will be explored in detail to understand the impact it poses on the overall security of the network and the firm. Various testing tools can be used along with manual testing techniques to exploit the security vulnerability further and place the CVSS score according to the priority of resolution. All of the vulnerabilities, any suspicious services or third-party components/plugins, and other aspects that require further attention will be listed out.
Exploitation
Till now, we’ve covered the steps for a network vulnerability assessment – now, we step into the first difference between a vulnerability analysis and penetration testing methodology. This is the actual phase of exploitation in order to understand how far each vulnerability can be taken to compromise the system and evaluate the true risk associated with each one.
At this stage, testers will attempt to gain access to the network through different devices, applications, firewalls, and through other weak points discovered so far to understand the impact. This phase takes the most time since automated testing by tools is complemented with manual-intensive testing techniques for understanding network security according to the context of the business logic adopted by the firm. Evidence will also be gathered for presenting proof-of-concept and the steps needed to make it occur again. Different methods such as credential harvesting, network sniffing, and exploiting common vulnerabilities will be adopted.
Some of the common tools used for the network penetration testing procedure are Nessus, Nexpose, Kali Linux, Metasploit, and nmap, along with a combination of any internally developed tools of the penetration testing company.
Preparing the Final Report
Pentesters are also required to provide the final report encompassing all of the findingsteps-in-a-network-penetration-testing-methodology/s of the network penetration testing procedure such as vulnerabilities, level of exploitation, criticality levels of each vulnerability, and the overall business impact of each if left unresolved. A good final report will possess clear language, provide actionable insights will adequate context for each vulnerability, and evidence for better understanding among technical and non-technical stakeholders.
After the final report provides remediation measures for the vulnerabilities discovered, most third-party penetration service companies provide after-testing services where they resolve doubts and concerns by sitting in with the internal IT team.
Network security is an essential part of the firm’s overall cybersecurity strategy which designates the importance of in-depth and periodic network penetration testing procedures. Moreover, the right network penetration testing methodology must be followed for optimal results and the best protection through the resolution of the vulnerabilities discovered.